Webhooks are very similar to Zapier triggers/events, except that you’ll use custom code to react to those events. Want code-free event notifications? Learn how to use Memberful with Zapier
Webhook process overview
Here’s an overview of the process by which Memberful sends webhooks to your application.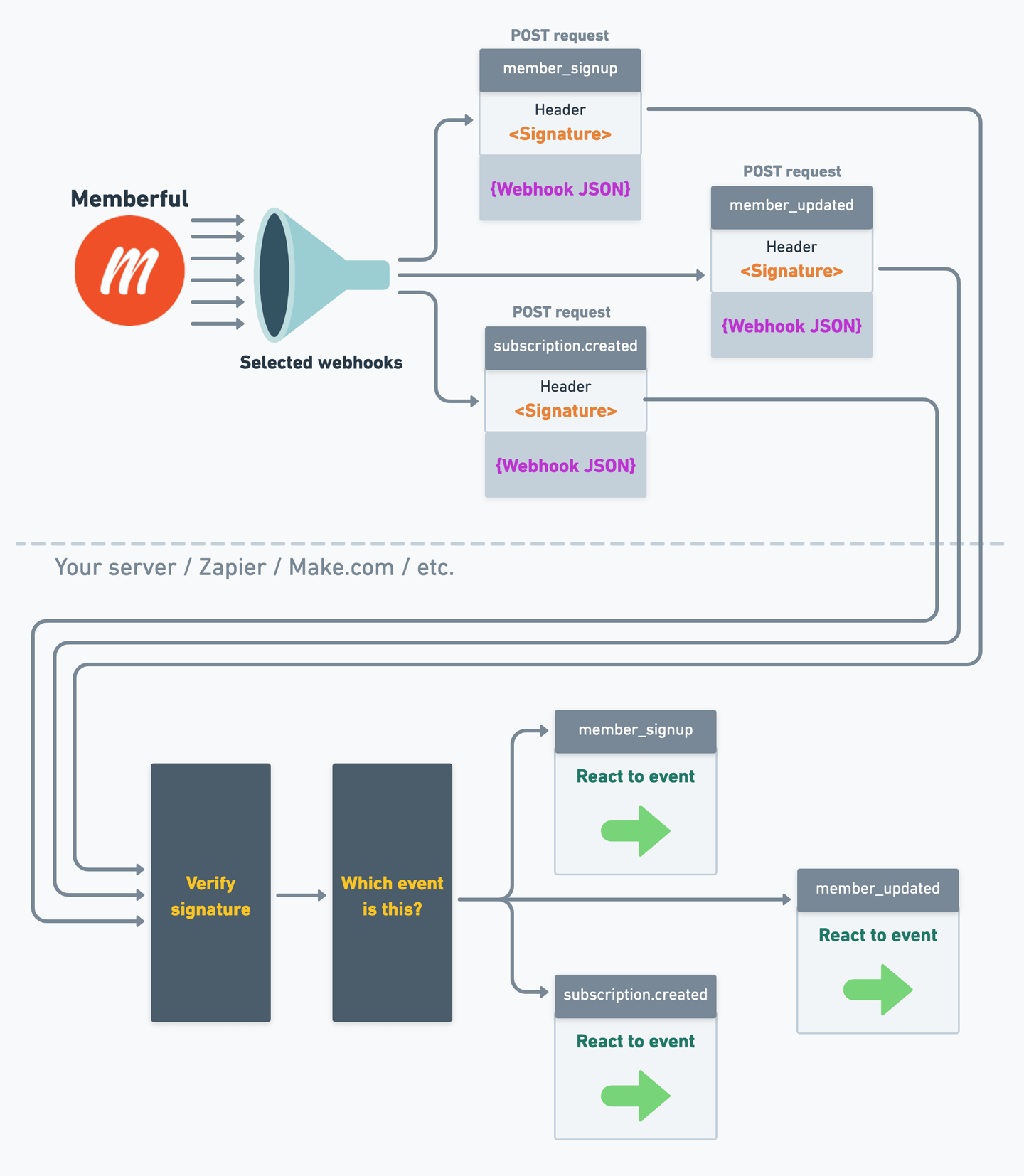
POST request with a header that contains a signature (to ensure it’s legitimate) and a JSON payload that contains the event data.
When your endpoint receives the webhook, it should verify the signature and process the event only if it’s legitimate.
Then, your endpoint can take whatever action is appropriate for each event type.
Set up a webhook
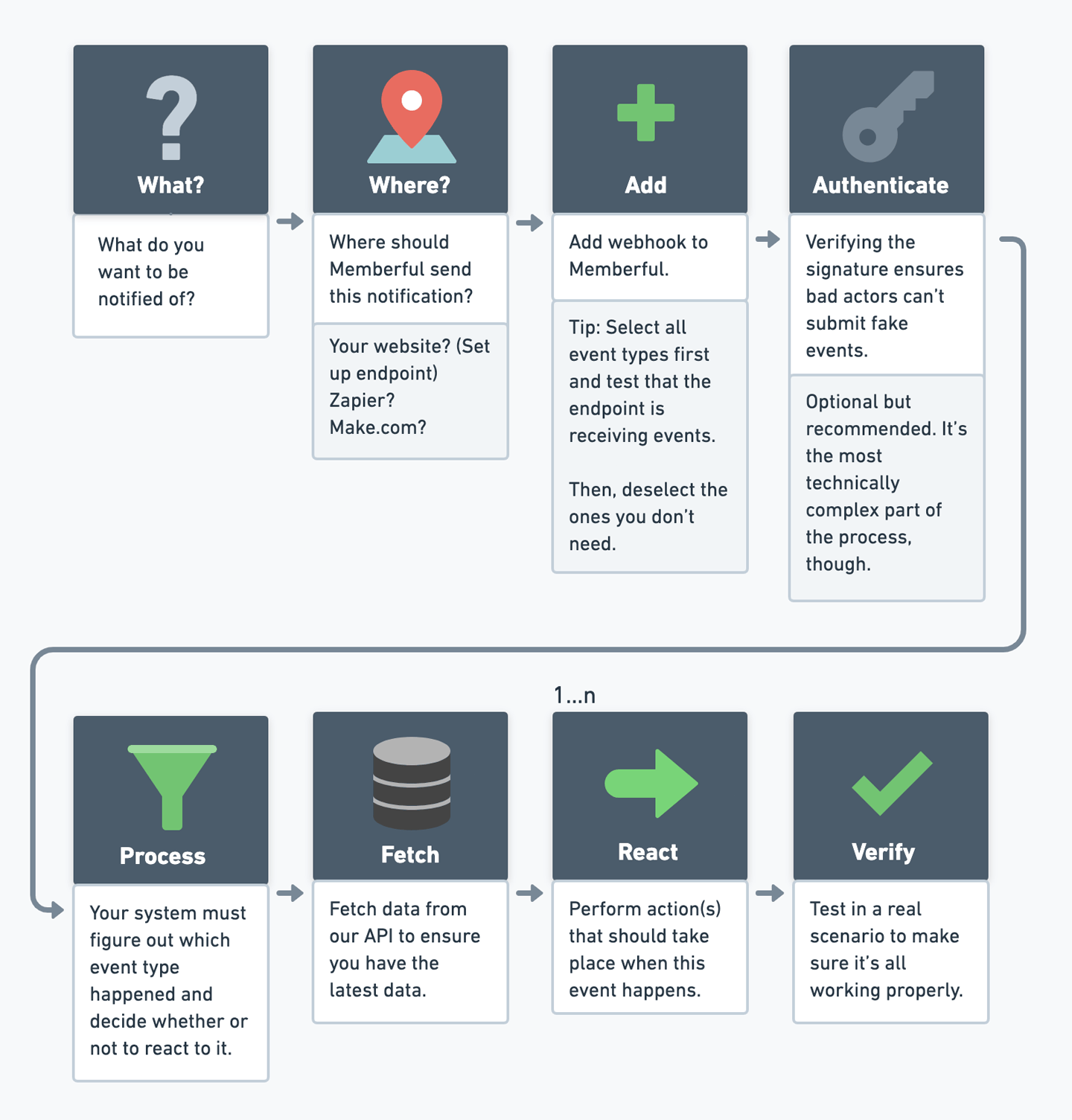
Create an endpoint
Create an endpoint where Memberful will send webhook notifications.
Create a webhook in Memberful
Create a webhook in Memberful, select the events you want to be notified about, and specify the endpoint URL. It would be a good idea to trigger a test webhook at this point to make sure your endpoint is working properly.
Implement verification
Implement verification of the webhook signature in your endpoint. This ensures that the webhook is legitimate and not a malicious request.
Fetch data from our API
Fetch data from our API to ensure you are acting on the latest data.
Create an endpoint
You’ll need to create an endpoint that will receive and process the webhooks. This can be an endpoint on your site/app or an external service like Zapier or Make.com. Memberful sends webhooks asPOST requests with a JSON payload, so it’s a good idea to ensure that your endpoint only responds to POST requests.
If you’re having trouble and want to find out whether or not Memberful is sending webhooks to your endpoint, you can use a service like Webhook.site to create a temporary endpoint that will log all requests that are received, in realtime.
Create and manage webhooks
To create and manage webhooks in Memberful, navigate to Settings → Webhooks in your Memberful dashboard. When creating or editing a webhook, you can specify the type of changes you want to be notified about. For example, you can specify that you ony want to be notified when a subscription is activated, deactivated, or renewed.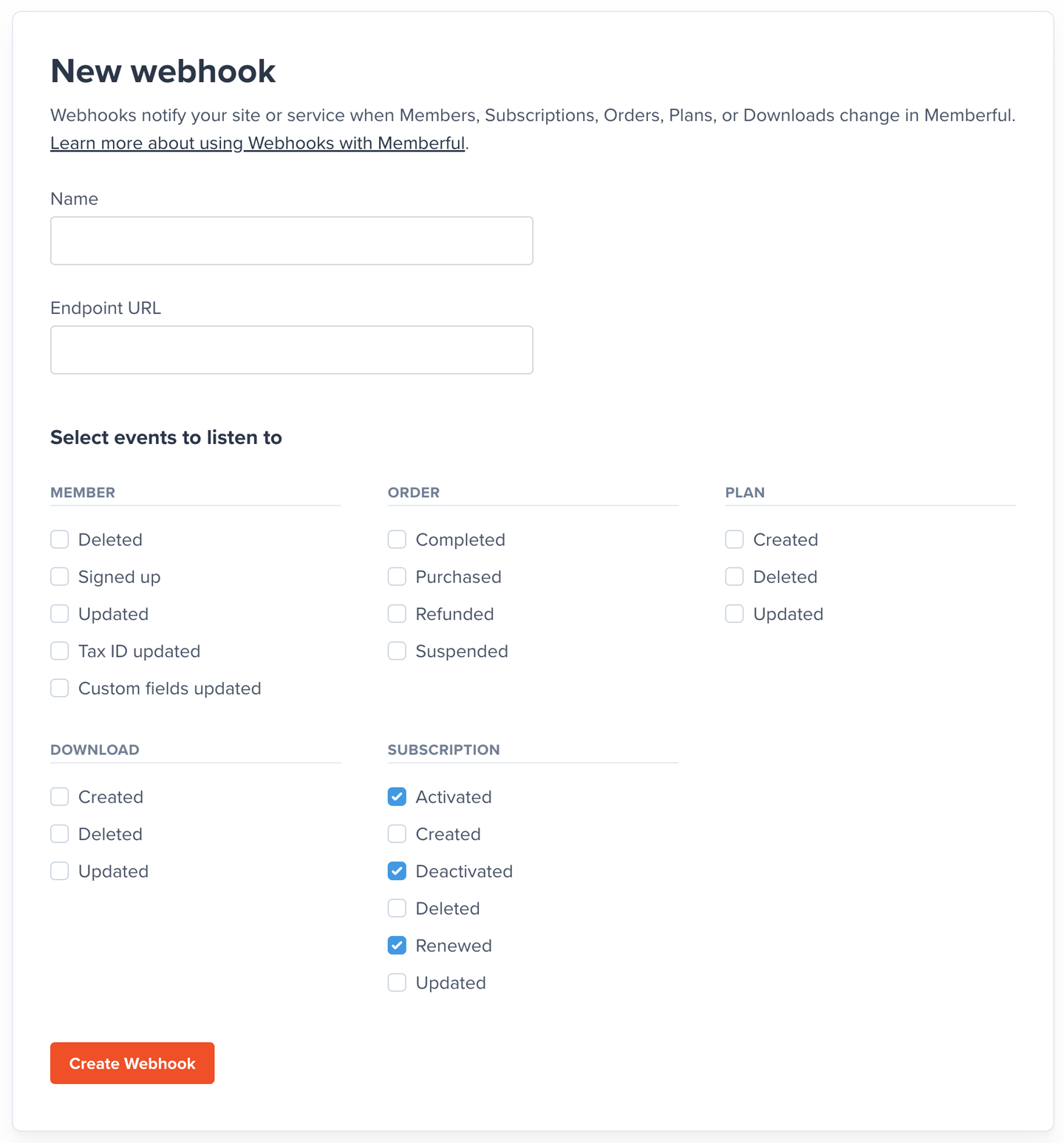
Fetch data from our API
When you receive a webhook, you should always fetch the latest version of the order/member/plan/download/etc. from Memberful’s API to avoid issues with the order in which webhooks arrive. Memberful does not guarantee delivery of events in the order in which they are generated.Verify requests
You’ll receive a secret key after you create a webhook endpoint. Memberful signs every request with anX-Memberful-Webhook-Signature header that combines your secret key and the request payload so you can verify that the request is coming from us (an impersonator wouldn’t know your secret key so they couldn’t fake this header).
To generate the header, Memberful computes a hash-based message authentication code (HMAC) with SHA-256, using your Webhook secret as the key and the webhook’s payload as the message.
To make sure the requests are coming from us, you should compute the HMAC signature yourself and compare it with the one that Memberful included in the header.
Here’s an example using Ruby on Rails: